Disclaimer: Don't hack anything where you don't have the authorization to do so. Stay legal.
Ever since I bought my first Android device, I wanted to use the device for WEP cracking. Not because I need it, but I want it :) After some googling, I read that you can't use your WiFi chipset for packet injection, and I forgot the whole topic.
After a while, I read about hacking on tablets (this was around a year ago), and my first opinion was:
"This is stupid, lame, and the usage of that can be very limited".
After playing one day with it, my opinion just changed:
"This is stupid, lame, the usage is limited, but when it works, it is really funny :-)"
At the beginning I looked at the Pwn Pad as a device that can replace a pentest workstation, working at the attacker side. Boy was I wrong. Pwn Pad should be used as a pentest device deployed at the victim's side!
You have the following options:
- You have 1095 USD + VAT + shipping to buy this Pwn Pad
- You have around 200 USD to buy an old Nexus 7 tablet, a USB OTG cable, a USB WiFi dongle (e.g. TP-Link Wireless TL-WN722N USB adapter works).
In my example, I bought a used, old 2012 Nexus WiFi. Originally I bought this to play with different custom Android ROMs, and play with rooted applications. After a while, I found this Pwn Pad hype again and gave it a shot.
I don't want to repeat the install guide, it is as easy as ABC. I booted a Ubuntu Live CD, installed adb and fastboot, and it was ready-to-roll. I have not measured the time, but the whole process was around 20 minutes.
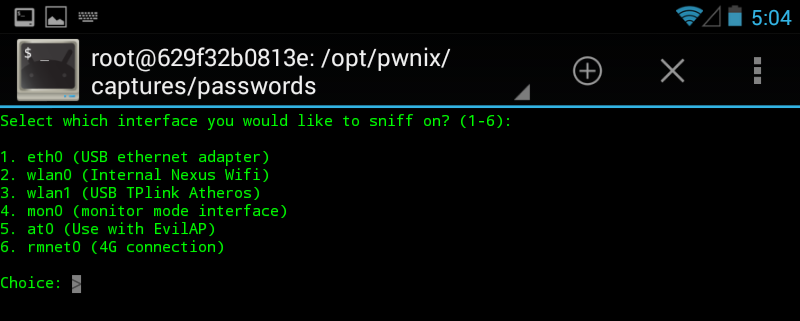
The internal WiFi chipset can be used to sniff traffic or even ARP poisoning for active MiTM. But in my case, I was not able to use the internal chipset for packet injection, which means you can't use it for WEP cracking, WPA disauth, etc. This is where the external USB WiFi comes handy. And this is why we need the Pwn Pad Android ROM, and can't use an average ROM.
There are two things where Pwn Pad really rocks. The first one is the integrated drivers for the external WiFi with monitor mode and packet injection capabilities. The second cool thing is the chroot wrapper around the Linux hacking tools. Every hacking tool has a start icon, so it feels like it is a native Android application, although it is running in a chroot Kali environment.
Wifite
The first recommended app is Wifite. Think of it as a wrapper around the aircrack - airmon - airodump suite. My biggest problem with WEP cracking was that I had to remember a bunch of commands, or have the WEP cracking manual with me every time I have to crack it. It was overcomplicated. But thanks to Wifite, that is past.
In order to crack a WEP key, you have to:
- Start the Wifite app
- Choose your adapter (the USB WiFi)
- Choose the target network (wep_lan in the next example)
- Wait for a minute
- PROFIT!
SSH reverse shell
This is one of the key functionalities of the Pwn Pad. You deploy the tablet at the Victim side, and let the tablet connect to your server via (tunneled) SSH.
The basic concept of the reverse shells are that an SSH tunnel is established between the Pwn Pad tablet (client) and your external SSH server (either directly or encapsulated in other tunneling protocol), and remote port forward is set up, which means on your SSH server you connect to a localport which is forwarded to the Pwn Pad and handled by the Pwn Pad SSH server.
I believe the best option would be to use the reverse shell over 3G, and let the tablet connect to the victim network through Ethernet or WiFi. But your preference might vary. The steps for reverse shells are again well documented in the
documentation, except that by default you also have to start the SSH server on the Pwn Pad. It is not hard, there is an app for that ;-) On your external SSH server you might need to install stunnel and ptunnel if you are not using Kali. The following output shows what you can see on your external SSH server after successful reverse shell.
root@myserver:/home/ubuntu# ssh -p 3333 pwnie@localhost
The authenticity of host '[localhost]:3333 ([127.0.0.1]:3333)' can't be established.
ECDSA key fingerprint is 14:d4:67:04:90:30:18:a4:7a:f6:82:04:e0:3c:c6:dc.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '[localhost]:3333' (ECDSA) to the list of known hosts.
pwnie@localhost's password:
_____ ___ _ ___ ___ _____ _____ ___ ___ ___ ___
| _ \ \ / / \| |_ _| __| | __\ \/ / _ \ _ \ __/ __/ __|
| _/\ \/\/ /| .` || || _| | _| > <| _/ / _|\__ \__ \
|_| \_/\_/ |_|\_|___|___| |___/_/\_\_| |_|_\___|___/___/
Release Version: 1.5.5
Release Date: 2014-01-30
Copyright 2014 Pwnie Express. All rights reserved.
By using this product you agree to the terms of the Rapid Focus
Security EULA: http://pwnieexpress.com/pdfs/RFSEULA.pdf
This product contains both open source and proprietary software.
Proprietary software is distributed under the terms of the EULA.
Open source software is distributed under the GNU GPL:
http://www.gnu.org/licenses/gpl.html
pwnie@localhost:~$
Now you have a shell on a machine that is connected to the victim network. Sweet :) Now Metasploit really makes sense on the tablet, and all other command-line tools.
EvilAP and DSniff
Start EvilAP (it is again a wrapper around airobase), choose interface (for me the Internal Nexus Wifi worked), enter an SSID (e.g freewifi), enter channel, choose whether force all clients to connect to you or just those who really want to connect to you, and start.
The next step is to start DSniff, choose interface at0, and wait :) In this example, I used a popular Hungarian webmail, which has a checkbox option for "secure" login (with default off). There are sooo many problems with this approach, e.g. you can't check the certificate before connecting, and the login page is delivered over HTTP, so one can disable the secure login checkbox seamlessly in the background, etc. In this case, I left the "secure" option on default off.
In the next tutorial, I'm going to show my next favorite app, DSploit ;)
Lessons learned
Hacking has been never so easy before
In a home environment, only use WPA2 PSK
Choose a long, nondictionary passphrase as the password for WPA2
Don't share your WiFi passwords with people you don't trust, or change it when they don't need it anymore
Don't let your client device auto-connect to WiFi stations, even if the SSID looks familiar
I believe during an engagement a Pwn Plug has better "physical cloaking" possibilities, but playing with the Pwn Pad Community Edition really gave me fun moments.
And last but not least I would like to thank to the Pwn Pad developers for releasing the Community Edition!
Related links- Top Pentest Tools
- Pentest Tools Github
- Hacking Tools For Windows
- Pentest Tools For Windows
- What Are Hacking Tools
- Hack Tools For Ubuntu
- Hackers Toolbox
- How To Hack
- Hack Tools For Windows
- Hacker Tools Online
- Kik Hack Tools
- Hack Tools
- Hack Tools Online
- Pentest Tools Alternative
- Hacking Tools Name
- Hacking Apps
- Hacker
- Hack Tools For Pc
- Pentest Tools Kali Linux
- Easy Hack Tools
- Hacker Tool Kit
- Hacking Tools Usb
- Hacking Tools Hardware
- Hacker Tools Mac
- Hacking Tools For Windows
- Hacking Tools Software
- Hacking Tools Name
- Hacking Tools For Kali Linux
- Pentest Tools Subdomain
- Hacker
- Pentest Tools For Android
- Ethical Hacker Tools
- Hacker Tools 2020
- Pentest Tools Url Fuzzer
- Hacker Tools Linux
- Pentest Tools Website
- Hacker Security Tools
- Best Pentesting Tools 2018
- Hacking Tools Name
- Pentest Tools Android
- Pentest Tools Apk
- How To Install Pentest Tools In Ubuntu
- Hacker Tools Apk Download
- Nsa Hack Tools
- Physical Pentest Tools
- Hacking Tools For Games
- Hacker Tools For Pc
- Pentest Tools List
- Hack Tools Mac
- Pentest Tools Online
- Usb Pentest Tools
- Hack Website Online Tool
- Hack Tools Online
- Hacking Tools For Kali Linux
- Pentest Tools Url Fuzzer
- New Hacker Tools
- What Is Hacking Tools
- Hack App
- Kik Hack Tools
- Hacker Tools Windows
- Pentest Tools Framework
- Pentest Tools Windows
- Free Pentest Tools For Windows
- Hack Tools For Windows
- Hack Tool Apk
- Top Pentest Tools
- Pentest Automation Tools
- Pentest Tools Port Scanner
- Pentest Tools Subdomain
- Game Hacking
- Pentest Tools Subdomain
- Free Pentest Tools For Windows
- Pentest Tools Linux
- Hacker Hardware Tools
- Hack Tools Download
- Growth Hacker Tools
- Blackhat Hacker Tools
- Hacker Tools For Mac
- Hacker Tools 2020
- Android Hack Tools Github
- Hacking App
- Top Pentest Tools
- How To Hack
- Wifi Hacker Tools For Windows
- Best Pentesting Tools 2018
- Pentest Reporting Tools
- Underground Hacker Sites
- Hacking Tools For Pc
- Hack Tools Online
- Top Pentest Tools
- Black Hat Hacker Tools
- World No 1 Hacker Software
- Hacking Tools Kit
- Hack App
- Hack Tools For Mac
- Hacker Tools Linux
- Hacker Tools 2019
- Hacker Tools Online
- Bluetooth Hacking Tools Kali
- Pentest Tools Open Source
- What Is Hacking Tools
- Growth Hacker Tools
- Pentest Automation Tools
- Hacking App
- Hacks And Tools
- Pentest Tools For Windows
- Pentest Tools Free
- Pentest Tools Review
- Hacker Tools Online
- Hack Tools Download
- Pentest Recon Tools
- Pentest Tools Online
- Install Pentest Tools Ubuntu
- Pentest Recon Tools
- Hack Tools
- Hack Tool Apk No Root
- Pentest Tools Port Scanner
- Hack Tools Download
- Hack Tools For Ubuntu
- Hack Tools Github
- Pentest Tools Kali Linux
- Ethical Hacker Tools
- Hacking Tools Windows 10
- Hacker Tools Github
- Hack Tools Online
- Hack Tools For Ubuntu
- Hacker
- Pentest Tools For Windows
- Hacker Tools Free
- Hacking Tools Hardware
- Blackhat Hacker Tools
- Pentest Tools List
- Android Hack Tools Github
- Pentest Tools Linux
- Hacking Tools Mac
- Hack Tools For Mac
- Tools 4 Hack
- Hacking Tools Software
- Hacking Tools Hardware
- Hack Tools
- Hacking Tools Windows 10
- Pentest Tools Apk
- Hacking Tools For Games
- Hacker Tools
- Nsa Hacker Tools
- Top Pentest Tools
- Top Pentest Tools
- Usb Pentest Tools
- Hacking Tools For Kali Linux
- Hack Apps
- Hacking Tools For Mac
- Physical Pentest Tools
- Hacker Tools Online
- Pentest Tools Port Scanner
- Pentest Tools Nmap
- Pentest Automation Tools
- Hack Tools Github
- Hacking Tools For Windows
- Hacking App
- Hack Tool Apk No Root
- Hacking Tools Online
- Pentest Tools Online
- Ethical Hacker Tools
- How To Make Hacking Tools
- Pentest Tools Kali Linux
- Hacker
- Hacker